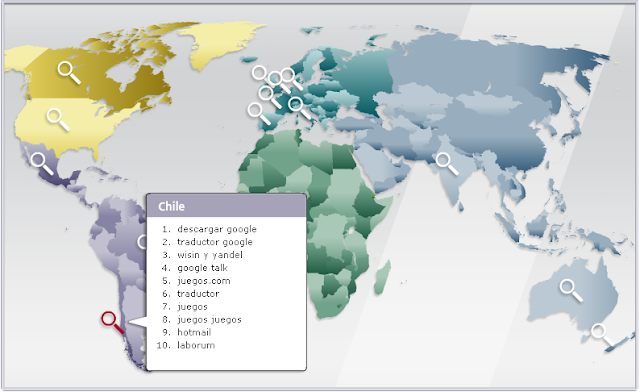
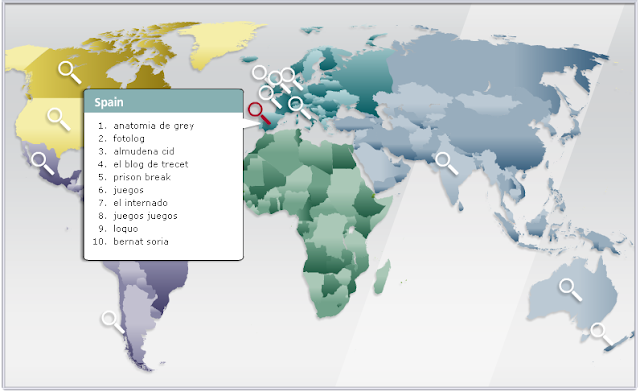
A group of scientists has demonstrated the possibility of stripping away the anonymity from significant numbers of users of popular social networking sites. Any technology allowing the identification of users of social networking sites, the collection of data about their habits and the prediction of their behavior can be used to cause harm. For example, such data can reveal a user’s sexual habits, or render somebody open to blackmail. But despite the fact that this threat is well known, very little has been done to prevent it.
The researchers demonstrated the possibility of this type of attack by identifying a user who was simply browsing the web. An attacker can probe the victim’s browser history for any URLs that may reveal membership of any social networking groups. By combining this information with previously collected data it is possible to identify any user of a social network who happens to visit the attacker’s website. In many cases, this allows the attacker running the malicious website to uniquely identify his visitors by the names which they use in their corresponding social networking profiles.
This type of attack requires very little effort to carry out and has the potential to affect many millions of registered social networking users who have group memberships.
Ref: iseclab.org/papers/sonda-TR.pdf